Nasza firma oferuje usługi w zakresie odzyskiwania danych
Firma Help-Dysk - odzyskiwanie danych Łódź
W dzisiejszych czasach dane są jednym z najważniejszych zasobów dla firm i osób prywatnych. Bez nich trudno sobie wyobrazić funkcjonowanie wielu branż, a utrata informacji może prowadzić do poważnych strat finansowych, a nawet zagrozić istnieniu przedsiębiorstwa. Dlatego też odzyskiwanie danych jest procesem, który wymaga zaangażowania specjalistów, którzy posiadają wiedzę i doświadczenie w dziedzinie informatyki oraz dysponują odpowiednim sprzętem.
Firma Help-Dysk to przedsiębiorstwo, które od wielu lat specjalizuje się w odzyskiwaniu danych z różnych nośników. Posiada ona siedziby w kilku krajach europejskich, co pozwala na szybką i skuteczną obsługę klientów z całego kontynentu. Co sprawia, że Help-Dysk jest najlepszą firmą w Europie w tej dziedzinie?
1.) Doświadczenie i wiedza specjalistów Zespół Help-Dysk składa się z wykwalifikowanych i doświadczonych specjalistów, którzy nieustannie podnoszą swoje kwalifikacje. Posiadają oni wiedzę i umiejętności, które pozwalają na odzyskiwanie danych z różnych nośników, w tym dysków twardych, kart pamięci, pendrive'ów czy urządzeń mobilnych. Dzięki temu są w stanie poradzić sobie nawet z najtrudniejszymi przypadkami.
2.) Najnowsze technologie i sprzęt Firma Help-Dysk inwestuje w najnowsze technologie i sprzęt, co pozwala na skuteczne odzyskiwanie danych. Posiada ona laboratoria wyposażone w specjalistyczny sprzęt, który umożliwia odzyskiwanie danych z uszkodzonych nośników. Dzięki temu firma jest w stanie poradzić sobie z bardzo złożonymi przypadkami, które wymagają zastosowania zaawansowanych technologii.
3.) Indywidualne podejście do klienta Firma Help-Dysk stosuje indywidualne podejście do każdego klienta, co oznacza, że analizuje ona każdy przypadek osobno i dobiera odpowiednie narzędzia i metody odzyskiwania danych. Dzięki temu firma jest w stanie zapewnić szybką i skuteczną pomoc, niezależnie od tego, jakie problemy napotka klient.
Odzyskiwanie danych z urządzeń mobilnych stało się w ostatnich latach bardzo ważne. Telefony komórkowe i smartfony przechowują wiele wartościowych informacji, takich jak wiadomości, kontakty, zdjęcia czy pliki, które są bardzo ważne dla użytkowników. Dlatego też, w przypadku ich utraty lub uszkodzenia, odzyskanie danych może być kluczowe.
Jedną z firm w Polsce, która zajmuje się odzyskiwaniem danych z telefonów i smartfonów, jest firma HELP-DYSK. Zespół ekspertów z tej firmy przede wszystkim kieruje się dobrem swoich klientów oraz szybkim odzyskaniem cennych danych. Jednym z cennych atutów firmy jest fakt, że jako jedna z nielicznych firm w Polsce, oferuje ona odzyskiwanie danych z fizycznego zrzutu pamięci telefonu lub smartfonu CHIP-OFF. Jest to bardzo ważne, ponieważ w przypadku problemów z oprogramowaniem, zastosowanie narzędzi, które nadpisują dane, może spowodować utratę danych. Wgranie oprogramowania do urządzenia, również może zmniejszyć możliwości odzyskania danych.
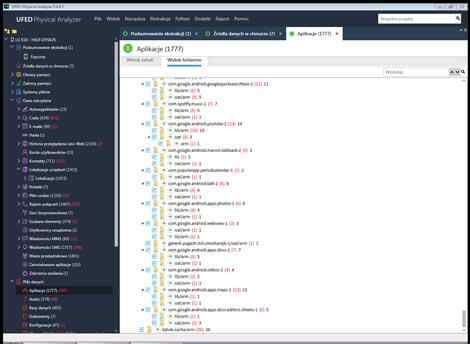
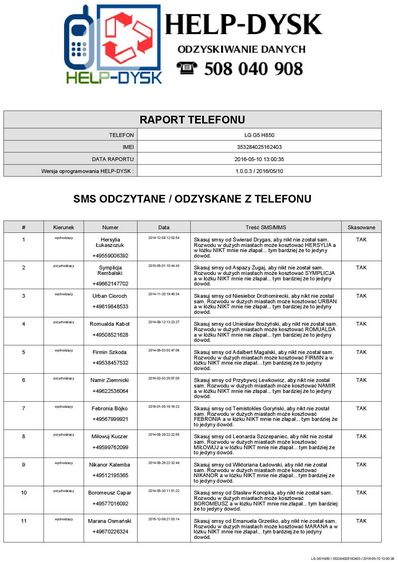
Proces odzyskiwania danych, jakim zajmuje się firma HELP-DYSK, jest bardzo skrupulatny i dokładny. Zespół ekspertów skupia się na sprawdzaniu fizycznego zrzutu pamięci telefonu lub smartfonów, pod kątem możliwości odzyskania danych. Wśród danych, które firma może odzyskać znajdują się: czaty, wiadomości z różnych aplikacji, kontakty, lokalizacje, pliki cookie, rejestr połączeń, sieci bezprzewodowe, szukane elementy, użytkownicy urządzenia, wiadomości mms, wiadomości sms, hasła, historia przeglądania sieci web, konta użytkowników, wieże przekaźnikowe, zainstalowane aplikacje, zdarzenia zasilania, oś czasu, pliki danych, aplikacje, audio, bazy danych, dokumenty, konfiguracje, obrazy, tekst, wideo, analiza aktywności i analiza telefonów. Zespół ekspertów dba o to, aby każdy możliwy sposób odzyskania danych został wykorzystany.
Firma HELP-DYSK oferuje również odzyskiwanie danych z różnych modeli telefonów, od tych starszych, po te najnowsze, także tych, które są zablokowane kodem, zalane lub uszkodzone fizycznie. Firma ta posiada wiedzę, sprzęt i doświadczenie potrzebne do efektywnego odzyskiwania danych z różnych urządzeń.
Warto zauważyć, że odzyskiwanie danych z telefonów i smartfonów jest procesem czasochłonnym i wymagającym dużej wiedzy technicznej oraz doświadczenia. Dlatego też warto zwrócić się do specjalistów, którzy zajmują się odzyskiwaniem danych z urządzeń mobilnych. Firmy, takie jak HELP-DYSK, posiadają odpowiedni sprzęt oraz wiedzę, która pozwala na skuteczne odzyskanie danych z różnych modeli telefonów i smartfonów.
Jednym z kluczowych aspektów, który wyróżnia firmę HELP-DYSK, jest fakt, że nie stosuje ona programów, które nadpisują dane do odzyskania. Jest to bardzo ważne, ponieważ nadpisanie danych może znacznie utrudnić lub wręcz uniemożliwić ich odzyskanie. Dlatego też zespół ekspertów z firmy HELP-DYSK skupia się na pracy z fizycznym zrzutem pamięci, co pozwala na zachowanie maksymalnej ilości danych.
Odzyskiwanie danych z urządzeń mobilnych może być kluczowe w wielu sytuacjach. Użytkownicy, którzy stracili ważne informacje, mogą skorzystać z usług firm takich jak HELP-DYSK, które oferują skuteczne i szybkie odzyskiwanie danych. Warto zwrócić uwagę na fakt, że odzyskiwanie danych jest procesem czasochłonnym, dlatego też im szybciej zwrócimy się o pomoc, tym większe szanse na skuteczne odzyskanie danych.
Podsumowując, firma HELP-DYSK oferuje kompleksowe i skuteczne usługi odzyskiwania danych z urządzeń mobilnych. Dzięki specjalistycznemu sprzętowi i doświadczeniu zespołu ekspertów, firma ta może odzyskać wiele cennych informacji z różnych modeli telefonów i smartfonów. Jeśli więc straciliście ważne dane, warto skorzystać z pomocy specjalistów, którzy skutecznie pomogą w odzyskaniu utraconych informacji. .
Dzięki tej metodzie możemy odzyskać wszystkie informacje zapisane i skasowane na telefonie.
Jesteśmy wstanie powiedzieć po analizie nośnika np kiedy był telefon przywrócony do ustawień fabryczny, ile zostało napisanych smsów z jakich kart numery IMSI, ITD
Skasowałeś informacje z aplikacji np WhatsApp, Viber, Facebook Messenger, Threema, Skype na telefonie zadzwoń do nas odzyskamy.
W telefonie zostają informacje skasowane nawet po okresie do 2 lat od skasowania danych.
Posiadamy wiedzę i sprzęt do odzyskania danych z uszkodzonych telefonów fizycznie.
DO ANALIZY TELEFON DOSTARCZASZ BEZ KARTY SIM !
Ważna informacja.
Uwaga: U nas dane odzyskiwane są ze zrzutu fizycznego pamięci
co daje większe możliwości w odzyskaniu utraconych danych.
ODZYSKUJEMY SMSY Z WYBRANEGO NUMERU TELEFONU
ODBLOKOWANIE TELEFONU
USUNIĘCIE HASŁA PINU WZORU
GOOGLE GMAIL
JEST TEŻ MOŻLIWOŚĆ USTALENIA
BLOKADY HASŁA PINU WZORU TELEFONU
Odczyt skasowanych SMS lub kontaktów odbywa się w ramach ekstrakcji fizycznej pamięci telefonu komórkowego czas trwania zależy od czasu trwania całego procesu ekstrakcji i waha się od jednej do czterech godzin.
- telefon nie włącza się
- telefon wibruje, nie włącza się
- telefon się nie włącza, ale wibruje odzyskanie kontaktów NOKIA
- telefon się nie włącza uszkodzony procesor odzyskanie kontaktów NOKIA np:(Nokia C5-00)
Odzyskiwanie danych z uszkodzonego telefonu
- uszkodzony bootloader
(brick, unbrick, fix HARD BRICKED)- uszkodzony dotyk
- uszkodzony wyświetlacz dotykowy
- uszkodzony wyświetlacz w telefonie
- telefon zablokowany hasłem (password), pin, pattern locks
- telefon zablokowany wzorem
- telefon zablokowany hasłem gmail LG, SAMSUNG, SONY, HTC, android
- telefon nie włącza się
- telefon wibruje, nie włącza się
- telefon się nie włącza, ale wibruje odzyskanie kontaktów NOKIA
- telefon się nie włącza uszkodzony procesor odzyskanie kontaktów NOKIA np:(Nokia C5-00)
Odzyskujemy wszystkie możliwe skasowane informacje w telefonie lub smartfonie.
Data Recovery
Data recovery is the way of getting back corrupted, debased, lost or formatted data from storage or files when the data put away in them cannot be accessed to in an ordinary manner. Documents can be lost because of the format or re-configuration of a storage, or files removed by a virus, sudden system failure or program failures. There are numbers of varieties of data recovery process It relies upon the conditions of the data loss and how it occurred. A file and the information about that file are stored in different places is the reason why data recovery is possible in the first place. By taking a look at the contrast between more established magnetic drive mediums and new strong state drives, which record information in various ways, is the way to understanding the recoveries of data.Damaged Phone recovery
Contacts and instant messages are constantly put away in the device's inner memory. Also, it can't be taken out or utilized with different gadgets. Furthermore, that is the reason when your device is broken without backups, and there aren't typical approaches to separate or reestablish the spared data on the device, at that point you may lose them for good. Nonetheless, it's no reason to worry cause you can get help from Third-party applications to recover erased information from broken cell phone effectively. As for Android, there are some PC applications to recover lost data and it’s really not that complicated. Even for someone normal person who doesn’t know how literally data extraction works.Damaged Phone recovery
Damaged SD Card Recovery
There is the greater part of situations when your SD card can't be opened typically and be gotten to of your information when the card gets harmed or undermined. To be completely forthright, it is the exact opposite thing that any users in the world want it to happen. I mean regardless of whether you take a stab at opening the SD card through PC, Windows will advise you that the card isn't accessible to the fact that the files or the documents are mixed up and ruined. In any case, it's not the apocalypse! Cause you can fix or repair a corrupted SD Card without data loss using some easy to come by applications like Windows cmd, Windows file explorer error checking section. Even there are some Third-Party Applications to do that for you.Recover deleted messages from your Android
It's human of us to inadvertently erase significant instant messages as a result of one single wrong tap or lose all the instant messages after a reset or framework crash. Along these lines, fortunately, it's as yet conceivable to recover the lost instant messages on Android phone as long they're not overwritten by new information. Which is why the must do is to turn on the airplane mode instantly. Cause the truth is after getting deleted, Android OS doesn’t delete the messages from its memory space. And as recommended, you’ll need some Third-party Application to recover the deleted messages for your Android device.Recover deleted messages from your Android Samsung
Recover deleted messages from your Android Huawei
Recover deleted messages from your Android LG
Recover deleted messages from your Android Sony
Recover deleted messages from your Android Xiaomi
Recover deleted messages from your iPhone
Deleted or lost some important messages from your iPhone? No worries! Your iCloud, iTunes got it covered. Indeed, you can restore the deleted messages without having a recourse to do anything difficult. You can also use some other Third-party apps to recover lost messages. It’s really up to you entirely without breaking a sweat.Recover deleted messages from your iPhone
Naprawa wszelkiego rodzaju plików video :
naprawa pliku różnych typów włączając MP4, 3GP, ASF, AVI, DV, FLV, M2TS, MKV, MOV, MPG, OGG, SMV, SVCD, TS, WMV, VCD itp.
naprawa pliku różnych typów włączając MP4, 3GP, ASF, AVI, DV, FLV, M2TS, MKV, MOV, MPG, OGG, SMV, SVCD, TS, WMV, VCD itp.
Informacja dla osób, które wykorzystały wszystkie darmowe i płatne programy z internetu.
Dalej masz problem dzwoń 508 040 908 odbudujemy blokową strukturę pliku filmów uszkodzonych.
Plik mp4,mov,avi, który nie chce się odtwarzać.
Naprawiamy również nagrania audio M4A wprowadzone przez firmę Apple.
Dalej masz problem dzwoń 508 040 908 odbudujemy blokową strukturę pliku filmów uszkodzonych.
Plik mp4,mov,avi, który nie chce się odtwarzać.
Naprawiamy również nagrania audio M4A wprowadzone przez firmę Apple.
Odzyskiwanie danych bezpośrednio z dysku z rejestratora DVR